I read the article in other website.
Victor Faur is young Romanian, who hack the computer system of NASA.
According the article, he is the leader of WhiteHat team. But Faur argued in his defense that he only hacked into those systems in order to prove taht they were vulnerable, and that he did not cause any damage to them.
And according to him,he only targeted those servers because their group held regular contest to determine who was more skilled, and could hack into the most secure systems.
Romanian law, if he had been found guity on all accounts, Faur would have risked a maximum sentence of 12 years in prison, compared to the 54 years of prison time he might have received if judged in the U.S.
One of the hacker's defense attorneys, Mircea Borza, said that they would appeal to a higher court because "we did not expect this sentence. "He claims that Faur was only guilty of unauthorized access to the systems, which he also admitted, but not of deleting, intercepting or altering any data.
So for me,I agree.
Because of hacking in the computer system. We all know this computer are inventions by those people who inventors. To create a fast information , communication and etc. and not hacking to a computer system, information or websites. What would happen to world, if all computer system are hacking?. So the data in the computer that should send or share will be interrupted, because of hacking.
Even the outside world like spacecraft, it no longer to communicate them or will be loss.
So if their is a Law for hackers in the other country and its for good who using the computer. And to those who hackers people will be punished or prison in the jail. Hackers people use your skill in how to create a program
Monday, January 30, 2012
Monday, January 16, 2012
Case study4
WHAT IS HASH COLLISION?
A hash collision, and is it really a concern for data safety in a system like Permabit Enterprise Archive.
collision or clash is a situation that occurs when two distinct pieces of data have the same hash value, checksum, fingerprint, or cryptographic digest.
Collisions are unavoidable whenever members of a very large set (such as all possible person names, or all possible computer files are mapped to a relatively short bit string. This is merely an instance of the pigeonhole principle.
A hash collision, and is it really a concern for data safety in a system like Permabit Enterprise Archive.
collision or clash is a situation that occurs when two distinct pieces of data have the same hash value, checksum, fingerprint, or cryptographic digest.
Collisions are unavoidable whenever members of a very large set (such as all possible person names, or all possible computer files are mapped to a relatively short bit string. This is merely an instance of the pigeonhole principle.
WHAT REALLY HAPPENS DURING HASH COLLISION?
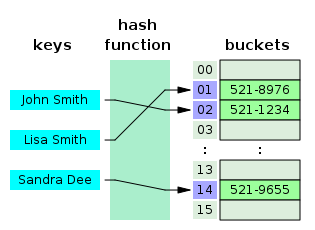
A hash table or hash map is a data structure that uses a hash function to map identifying values, known as keys (e.g., a person's name), to their associated values (e.g., their telephone number). Thus, a hash table implements an associative array. The hash function is used to transform the key into the index (the hash) of an array element (the slot or bucket) where the corresponding value is to be sought.| Type | unsorted dictionary | |
|---|---|---|
| Invented | 1953 | |
| Average | Worst case | |||||||
| Space | O(n)[1] | O(n) | ||||||
| Search | O(1 + n/k) | O(n) | ||||||
| Insert | O(1) | O(1) | ||||||
| Delete | O(1 + n/k) | O(n) | ||||||
Monday, January 9, 2012
Base in my understanding if computers block from connecting to security Web sites, and download a Trojan. if they have no computers ma wawalan nang silbi ang lahat, And return to the past day. People should patch their systems to close the hole in Windows they have a many people sad because in this year we are high Technology,
Subscribe to:
Posts (Atom)